You may wonder what the screen below has to do with the system value QSECURITY. A change in this system value was part of the announcement of IBM i 7.5, which had a strong focus on security. Level 20 is no longer supported and a new system is shipped with level 40. Setting your system to level 10, no system enforced security, has not been possible for several releases.
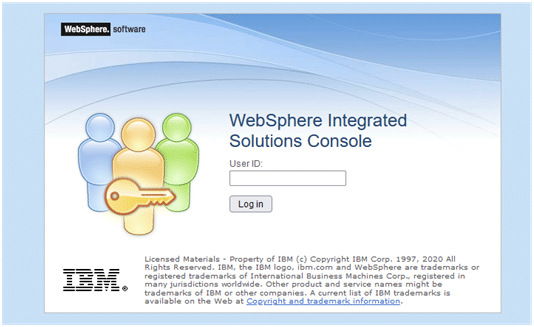
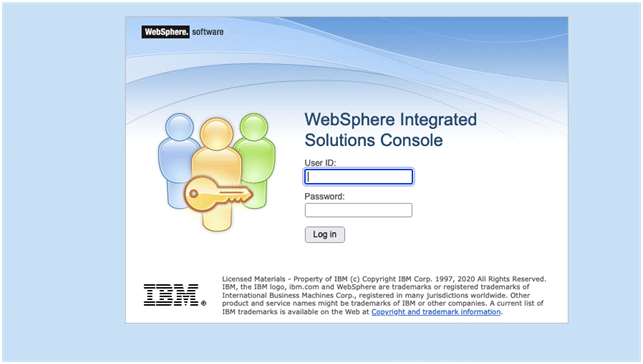
When looking at the above login screen, as if the old days have returned, any value for the User ID is accepted to enter the console. So once you are able to get connected to this console you are in. The argument that nobody is aware of the port used is what is called “security by obscurity”. Not the best practice regarding security to put it mildly!
If Websphere Applications Server is used on your box to run applications now is a good time to start securing them. So once you have entered a string for the User ID on this console, any value will do, it is time to make some changes.
- Select “Global security” under “Security”:
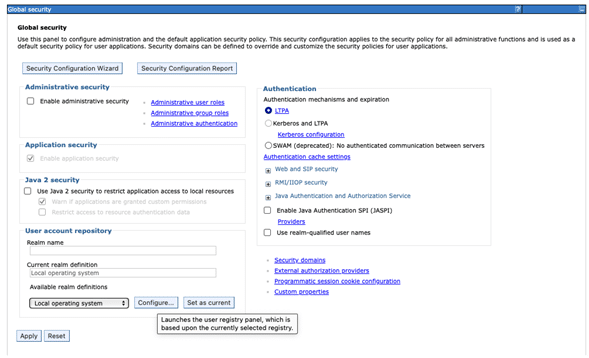
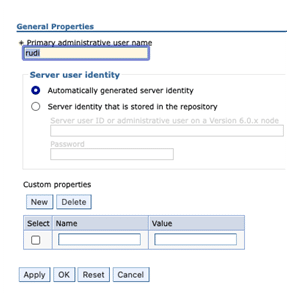
2. Select the “Configure” button and enter an IBM i Userprofile name as the “Primary administrative user name”:
3. Click OK.
4. Check the box “Enable administrative security” and select “Administrative user roles” and press the “Add…” button:
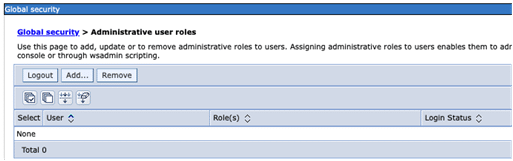
5. Use the “Search” button and when needed increase the number of the “Maximum results to display”. Select the appropriate IBM i Userprofiles and assign the Role(s). Please keep in mind then more than one role is allowed and if assistance is needed use the help panel. The “More information about this page” link will open up page containing the information shown below:

6. When ready press the “OK” button and press the “Apply” button of the Global Security panel
7. When you do so a window will be displayed looking similar to this:
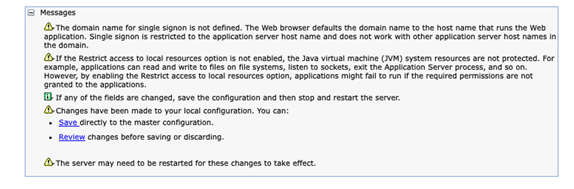
8. All that is left now to do is to restart your Server, when doing this using Web Administration for i, you will notice that the added security already kicks in:
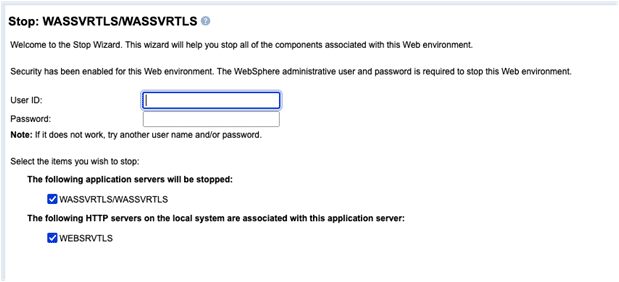
Credentials need to be entered in order to be allowed to stop the server.
After the restart of the Websphere your Console will look like this:
Protecting a server from unauthorized access is a no-brainer. Figuring out how to secure a Websphere Application server has to be done. I do not consider myself a Websphere expert so I called for help to get this done. When testing this setup I first did it in a test environment, once happy with the results I moved it into production. When reading this article, if you think this can be done in a better way please leave some comments behind. Helping other IBM i users, is that not what makes the IBM i community so strong?



Leave a Reply